
Before, using the command sudo netdiscover, scan our local network to find tenderfoot IP.

I started by scanning the target machine for any open ports and services running on those ports using the Nmap tool.
nmap -p- -A <IP>
Start with a little dirb scan on the http website:

And we found an interesting /entry.js who gives us this user in source-code : monica. Don’t forget it
Let’s start a new web enumeration. Download this wordlist and use it with gobuster.
gobuster dir --url http://<IP>/ --wordlist=/home/kali/Documents/big-dirbuster.txt -x js,php,txt,html,/ -t 100
In /fotocd source-code, we found this :

It’s a brainfuck code. Decode ti with this online tool. It gives us the following message :
=================
JDk5OTkwJA==
=================Did you found username ?
if yes:
Then you have cred. of one user, enter into user account
by ssh port. syntax:{ssh username@IP}
if not:
Then enumerate more :)
G00D LUCK !
We have one username, let’s decode the base64 code.
echo "JDk5OTkwJA==" | base64 -d
>$99990$Now we have username and password for ssh login : monica:$99990$

Open user1 flag :

To list all file in /monica, use the following command. -R allows to list subdirectories recursively.
ls -RaWe found a note.txt

Open it :

note.txt gives us the password to unzip joey.zip. Download joey.zip and unzip it with the command unzip joey.zip and the password #9175.
Now wee need to crack gift.zip, we are going to use frackzip with the rockyou.txt list.
fcrackzip -u -D -p '/home/kali/Documents/rockyou.txt' gift.zip
The extracted message tells us to find SUID or binaries. Using this command :
find / -type f -perm /6000 -ls 2>/dev/null
We run it and a bash shell spawn.
/opt/exec/chandler
Now cd /home/chandler/.cache/ . 3 files, open note.txt :

Decode the base32 password :
echo “OBQXG43XMQ5FSMDVINZDIY3LJUZQ====” | base32 -d
>passwd:Y0uCr4ckM3And it’s time to be root. Exit our shell as chandler by authenticating as chandler with su chandler and password Y0uCr4ckM3. With sudo -l we see that we can execute ftp as root. On this site, we found a exploit with ftp, let’s use it :

cd /root
cat *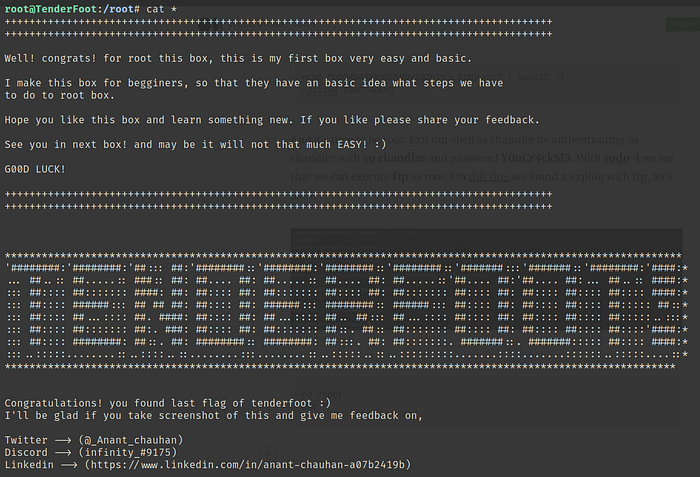
…well done
